[5/2/15 I may have been mistaken about the running inside virtualization and that is probably normal livecd messages. There is still something amiss with the different ps axu(s) – it does at least make me very suspicious since I can’t think of any reason why that would happen other than nasty. I’m also surprised that this system is so difficult to boot into OpenBSD. You can’t be too paranoid, or can you?]
I’ve got an AMD64 thin client as a gateway / router that also runs a tor relay. It usually runs dnsmasq but has been running the more conventional dhcpd and named recently. It uses a small camera-style flash card as a hard drive running current and patched OpenBSD. My internal network connects to this through a switch. I run firewalls on all machines – pf on this of course and usually arno-iptables-firewall on debian boxes. This box currently has an uptime of over 59 days.

Just recently I’ve had a hard drive fail on my desktop debian machine. I was very surprised at this since it’s very low mileage and being debian linux it hardly ever gets powered down. It appeared to have many and increasing terrible errors that also seemed to jump about whenever I tried e2fscking them. I can’t help but suspect that GCHQ contributed to the apparent demise of this drive.
My new replacement drive arrived yesterday and I had decided to install an OpenBSD xfce desktop. None of the OpenBSD install cds were recognised. What’s going on here?
At the OpenBSD box:
# ps axu | grep bin
root 1 0.0 0.0 744 148 ?? Is 23Nov14 0:01.16 /sbin/init
_syslogd 12341 0.0 0.1 756 876 ?? I 23Nov14 0:08.61 /usr/sbin/sys
_iscsid 10832 0.0 0.1 624 548 ?? Is 23Nov14 0:00.00 /usr/sbin/isc
root 17049 0.0 0.1 1068 1100 ?? Is 23Nov14 0:00.04 /usr/sbin/ssh
_sndio 1059 0.0 0.0 712 344 ?? I<s 23Nov14 0:00.00 /usr/bin/sndi
root 25566 0.0 0.1 904 1092 ?? Ss 23Nov14 0:09.31 /usr/sbin/cro
< (xterm widened) >
# ps axu | grep bin
root 1 0.0 0.0 744 148 ?? Is 23Nov14 0:01.16 /sbin/init
_syslogd 12341 0.0 0.1 756 876 ?? S 23Nov14 0:08.61/usr/sbin/syslogd
_iscsid 10832 0.0 0.1 624 548 ?? Is 23Nov14 0:00.00 /usr/sbin/iscsid
root 17049 0.0 0.1 1068 1100 ?? Is 23Nov14 0:00.04 /usr/sbin/sshd
_sndio 1059 0.0 0.0 712 344 ?? I<s 23Nov14 0:00.00 /usr/bin/sndiod
root 25566 0.0 0.1 904 1092 ?? Ss 23Nov14 0:09.31 /usr/sbin/cron
_tor 18528 0.0 2.8 21700 25344 ?? S< 23Nov14 1927:49.62 /usr/local/bin/tor
That can’t be right – that tor only appears in the second and subsequent ps axu(s). Having huge difficulty i.e. it is impossible, to install OpenBSD to my desktop machine. They’re pwned.
OpenBSD doesn’t install under a Linux virualization ‘wrapper’. Linux runs under Linux virtualization, OpenBSD won’t – at least not under this virtualization.
“NET: Registered protocol family 17
mpls_gso: MPLS GSO support” it reads – it’s embedded Linux.
It appears to be a very small wrapper in IPv6 coming from the OpenBSD router / gateway. My laptop starts complaining that BIOS has been changed – not seen that message before. The tor router relay is stopped pretty sharpish.
GCHQ? Well my connection to my ISP is to their ‘audit’ machine. I guess that means GCHQ. My close friend’s car was hours late back from it’s first service – shouldn’t the first service only be oil and filter, a half hour job? After that it was clear that cops could hear everything said in that car and were often waiting for us to arrive. A friend who I was once close to had the ‘Water Board’ round to check his taps. He remarked that she was well-presented. I’ve noticed that local ‘Scientific Investigation’ policewomen are well-presented. Oh, and we had a deep cover spy at our anti-casualisation group meetings. He was also at a pre-G8 2005 meeting. I think that he was Met, very interested in me and an apparent dirty, hairy anarchist cop.
I was using a password 29 characters long. My guess is that they used my mobile to map my keyboard – different characters sound different and there are differences in the time I take to reach them. Or they could have watched (spied) through the window.
I don’t know if they wanted me to find this or not. I met someone from GCHQ in the Bunch of Grapes one Friday afternoon many years ago. It’s their job, it’s what they do.
I watched this a few hours earlier. You may get lost after the first 10 minutes or so. 30 to 37 minutes or so is good for politicians.
Can’t copy embed code. Bloody GCHQ. Bruce Schneier at MIT: https://www.youtube.com/watch?v=QXtS6UcdOMs
I’m listening to this at the moment
but while I’m listening to this I want to explain a far greater danger than terrorism that I face almost daily because you see, I am a cyclist.
Yesterday I was almost mown down by a motorist that was on the wrong side of the road and almost mowed me down. He had not seen me because he was texting.
Motorists on mobile phones are lethal to cyclists – a far greater danger than any supposed attacks by ‘terrorists’. I can attest that there is a far greater danger to people – pedestrians, cyclists and motorcyclists – than terrorism. We need a sense of proportion, to be measured and to asses issues. As a cyclist, I am telling you it is far more dangerous than any fake manufactured, terrorism nonsense. I accept that there are a very few terrorists – usually insane. How can they be anything other than insane? But, they are caught up in the terrorist narrative. Cycling and being a pedestrian is far more dangerous.
Where is the international campaign against motorists using mobile phones? Surely NASA, GCHQ can catch these ‘t*******ts’? Don’t they cause terror to ordinary people and kill indiscriminitely? Actually, yes they do. And far more than this terrorism BS.
There are very few terrorist. Yes they should be pursued. There is fake, manufactured terrorism which is still terrorism pursued by nation-states and criminal cabals. There are also a few poor sods caught up in the terrorism narrative but let’s get it in perspective.
Indiscriminite drones. Stop it.
Ok, er, cycling is nothing compared to rockets from a drone. It’s much the same that it’s totally undeserved but I reckon a drone is far more lethal
– he’s talking about speed limits now
struck by lightening
I suggest that you watch the Greenwald vid. still long to go – talking about inscenity now
Talking about terrorism defined as what Muslims do. We had this in Uk recently with the car driven into council offices up North which then exploded. Strangely enough that wasn’t a car bomb and was reported on the news as most definitely not terrorism …
Intermission: I take advantage of this intermission to point out out that I do magick: that I have converted water into wine with the assistance of fruit, sugar and yeast. I made Melomel for the first time this year and I think that it may have been the first medicine (Meddygon Myddfai). Untreated, unadulterated honey and currant fruits worked really well. It was like a universal medicine – anything that was wrong with you it cured. I believe that it is possible to keep bees without exploiting them.
OK, intermission over.
<snip>
22/1/15 2.40am At least they know that I’m not into CP. I wish that they would go for the ones that are (and more). Actually, I want them to go for the people that abuse children. My understanding of GCHQ’s purpose is that it’s outside their remit. I think that GCHQ is military and concerned with defence. Can we change that so that they catch paedos?
better now ;)

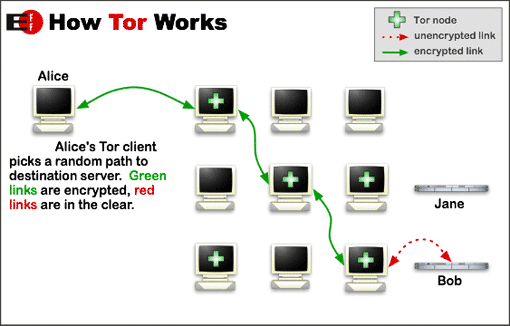 The bad news
The bad news