OpenBSD is widely regarded as the most secure operating system. Today is the release date of the latest release OpenBSD 5.4. You’ll need to give it a few hours because it’s not yet 1/11 in Canada.
OpenBSD is secure because it is continually security audited. It is absolutely ideal for firewall/routers because of it’s advanced pf packet filter. It’s best suited for servers but also performs well on desktops and multimedia machines.
Other geeky things I’ve been doing lately
Learning C programming properly. C is all about pointers and indirection. It seems to be taught totally the wrong way. Pointers are key and all else follows …
I recapped a motherboard. You don’t need a new machine nowadays and I was pleased to revive a machine for a friend’s parents. It’s good to save a computer from the skip. I solder badly because I don’t do it often enough but I obviously solder well enough.
I replaced a Sempron LE-1150 with a really fast Athlon X2. Now it rocks.
[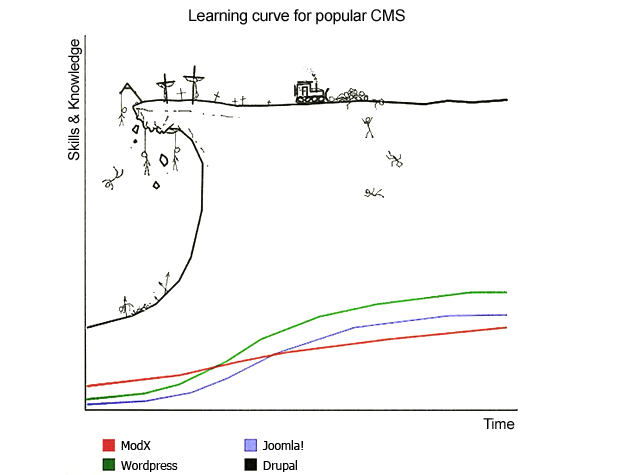 11/11/13 I’ve been trying to learn Drupal 7. Drupal is a Content Managment System (CMS) which also claims to be a CMS framework. A CMS is used to build websites and Drupal is used to build many of the most complex and advanced websites. As the diagram shows, Drupal is difficult to grok. My experience is that it’s counterintuitive and opposed to many of the principles of programming e.g. the use of global variables. But then it’s not programming of course – it’s an application for developing websites.
11/11/13 I’ve been trying to learn Drupal 7. Drupal is a Content Managment System (CMS) which also claims to be a CMS framework. A CMS is used to build websites and Drupal is used to build many of the most complex and advanced websites. As the diagram shows, Drupal is difficult to grok. My experience is that it’s counterintuitive and opposed to many of the principles of programming e.g. the use of global variables. But then it’s not programming of course – it’s an application for developing websites.
I did try Joomla and WordPress but it looks like Drupal is what I need to build the websites I want. I think it may be that you just have to learn the Drupal way. Just lately I’ve been doing some maintenance to this blog and realised that WordPress produces an awful lot of dead links which are no good to anyone. I’m thinking of converting this blog to Drupal soon and get some practice in.
There’s some weirdness about this post – not allowing me to edit it as I normally would. I’ve had to use a different browser because it simply appeared totally blank in the browser I normally use but yet it appears published fine. Weird.]
[9/12/13 I’ve been repairing analogue radios just recently. It’s surprising what some contact cleaner, compressed air and a vacuum cleaner can achieve. I still need to repair my favourite radio which was second-hand and well used when I got it about 1999. It will need some soldering but some radios are special.]
Some geeky tips
Use strong passwords. I particularly like long passwords because I know about brute-forcing.
Backup.
Get a real operating system. Linux livecds can help.
[More geeky tips. This could go on and on.
Firewall. Firewall on all interfaces especially on laptops and mobile devices. Lock it down.
Wireless should be considered insecure.
[6/11/13 The Guardian has published a Guide to Tor. The latest Tor browser bundle should be used and care should be taken. People have been caught-out accessing web-based email by not appreciating how it works. It should not be used for anything that divulges personal info and there’s not really much point in watching Youtube through Tor. If you’re in a repressive country it’s worth using. Basically, it hides what you’re looking at. [edit: It’s likely to get past broad political internet censorship. ]
If you have geek competence and spare resources please consider running a Tor relay as I do. There are certain dangers involved in running an exit node (relay) which do not apply to intermediate nodes.]
[4/11 What was I not thinking about? Mobile phones are designed to be mobile bugs.
… and here are the regulations from the ILETS / ENFOPOL affair of the 90s. These regulations are demands made by law enforcement authorities of the capabilities needed to infiltrate communications. Essentially, these law enforcement demands are design requirements for communication systems. You will notice that these requirements date from the mid 1990s. It’s probably safe to assume that they have been implemented by now. [Later edit: These regulations were intended particularly at mobile devices: phones at that time e.g. the reference to location. These regulations are bound to have been updated in the same culture of secrecy for technological developments since.]
COUNCIL RESOLUTION of 17 January 1995 on the lawful interception of telecommunications
(96/C 329/01)
Official Journal C 329 , 04/11/1996 p. 0001 – 0006
…
Annex: Requirements
This section presents the Requirements of law enforcement agencies relating to the lawful interception of telecommunications. These requirements are subject to national law and should be interpreted in accordance with applicable national policies. Terms are defined in the attached glossary.
1.Law enforcement agencies require access to the entire telecommunications transmitted, or caused to be transmitted, to and from the number or other identifier of the target service used by the interception subject. Law enforcement agencies also require access to the call-associated data that are generated to process the call.
1.1.Law enforcement agencies require access to all interception subjects operating temporarily or permanently within a telecommunications system.
1.2.Law enforcement agencies require access in cases where the interception subject may be using features to divert calls to other telecommunications services or terminal equipment, including calls that traverse more than one network or are processed by more than one network operator/service provider before completing.
1.3.Law enforcement agencies require that the telecommunications to and from a target service be provided to the exclusion of any telecommunications that do not fall within the scope of the interception authorization.
1.4.Law enforcement agencies require access to call associated data such as:
1.4.1.signalling of access ready status;
1.4.2.called party number for outgoing connections even if there is no successful connection established;
1.4.3.calling party number for incoming connections even if there is no successful connection established;
1.4.4.all signals emitted by the target, including post-connection dialled signals emitted to activate features such as conference calling and call transfer;
1.4.5.beginning, end and duration of the connection;
1.4.6.actual destination and intermediate directory numbers if call has been diverted.
1.5.Law enforcement agencies require information on the most accurate geographical location known to the network for mobile subscribers.
1.6.Law enforcement agencies require data on the specific services used by the interception subject and the technical parameters for those types of communication.
2.Law enforcement agencies require a real-time, fulltime monitoring capability for the interception of telecommunications. Call associated data should also be provided in real-time. If call associated data cannot be made available in real time, law enforcement agencies require the data to be available as soon as possible upon call termination.
3.Law enforcement agencies require network operators/service providers to provide one or several interfaces from which the intercepted communications can be transmitted to the law enforcement monitoring facility. These interfaces have to be commonly agreed on by the interception authorities and the network operators/service providers. Other issues associated with these interfaces will be handled according to accepted practices in individual countries.
3.1.Law enforcement agencies require network operators/service providers to provide call associated data and call content from the target service in a way that allows for the accurate correlation of call associated data with call content.
3.2.Law enforcement agencies require that the format for transmitting the intercepted communications to the monitoring facility be a generally available format. This format will be agreed upon on an individual country basis.
3.3.If network operators/service providers initiate encoding, compression or encryption of telecommunications traffic, law enforcement agencies require the network operators/service providers to provide intercepted communications en clair.
3.4.Law enforcement agencies require network operators/service providers to be able to transmit the intercepted communications to the law enforcement monitoring facility via fixed or switched connections.
3.5.Law enforcement agencies require that the transmission of the intercepted communications to the monitoring facility meet applicable security requirements.
4.Law enforcement agencies require interceptions to be implemented so that neither the interception target nor any other unauthorized person is aware of any changes made to fulfil the interception order. In particular, the operation of the target service must appear unchanged to the interception subject.
5.Law enforcement agencies require the interception to be designed and implemented to preclude unauthorized or improper use and to safeguard the information related to the interception.
5.1.Law enforcement agencies require network operators/service providers to protect information on which and how many interceptions are being or have been performed, and not disclose information on how interceptions are carried out.
5.2.Law enforcement agencies require network operators/service providers to ensure that intercepted communications are only transmitted to the monitoring agency specified in the interception authorization.
5.3.According to national regulations, network operators/service providers could be obliged to maintain an adequately protected record of activations of interceptions.
6.Based on a lawful inquiry and before implementation of the interception, law enforcement agencies require: (1) the interception subject’s identity, service number or other distinctive identifier; (2) information on the services and features of the telecommunications system used by the interception subject and delivered by network operators/service providers; and (3) information on the technical parameters of the transmission to the law enforcement monitoring facility.
7.During the interception, law enforcement agencies may require information and/or assistance from the network operators/service providers to ensure that the communications acquired at the interception interface are those communications associated with the target service. The type of information and/or assistance required will vary according to the accepted practices in individual countries.
8.Law enforcement agencies require network operators/service providers to make provisions for implementing a number of simultaneous intercepts. Multiple interceptions may be required for a single target service to allow monitoring by more than one law enforcement agency. In this case, network operators/service providers should take precautions to safeguard the identities of the monitoring agencies and ensure the confidentiality of the investigations. The maximum number of simultaneous interceptions for a given subscriber population will be in accordance with national requirements.
9.Law enforcement agencies require network operators/service providers to implement interceptions as quickly as possible (in urgent cases within a few hours or minutes). The response requirements of law enforcement agencies will vary by country and by the type of target service to be intercepted.
10.For the duration of the interception, law enforcement agencies require that the reliability of the services supporting the interception at least equals the reliability of the target services provided to the interception subject. Law enforcement agencies require the quality of service of the intercepted transmissions forwarded to the monitoring facility to comply with the performance standards of the network operators/service providers.
22/7/14 My stats show that this is the most popular post – probably because of the ILETS / ENFOPOL quote above.
Got a spares or repair box off eBay cheap and swaped the processor. It rocks – quad core, 2T hard drive and I only ever use a small part of the memory.
Learning django at the moment and hoping to build a site using it soon. Python is good.
Everything wireless strikes me as fantastically insecure. Normal computer users are going to be vulnerable to evil twins at public hotspots. What about wireless keyboards? That’s a keyboard transmitting what keys are pressed. I don’t know but would doubt that encryption is used.